What is a subnet? A complete guide to subnetting, VPNs, and network security

A subnet is a key concept in networking that involves dividing a network into smaller segments. This allows networks to be structured so devices and services can communicate efficiently and securely.
In this guide, we’ll explain the fundamentals of subnets, how they’re calculated, how they interact with virtual private networks (VPNs), and how they affect overall network security.
Understanding subnets in networking
 Subnets are essential for organizing, maintaining, and securing networks. Here’s a look at what they are, how they work, and what key benefits they offer.
Subnets are essential for organizing, maintaining, and securing networks. Here’s a look at what they are, how they work, and what key benefits they offer.
What is a subnet? Definition and core concepts
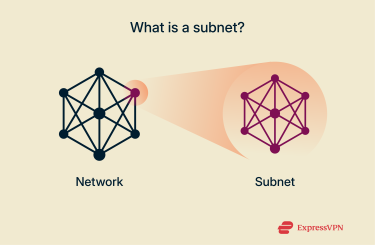
A subnet (short for subnetwork) is a smaller, logical segment of a network. “Logical” in this case means the subnet is created by dividing a network’s Internet Protocol (IP) address range into sections rather than physically separating devices.
Each subnet runs as an independent mini-network and uses routers and subnet masks to manage communications with other subnets, systems, and online services.
How subnets work to segment networks
Networks use IP addresses to communicate and share data. Each network has a specific range of IP addresses, and every connected device gets a unique one that identifies it. Subnetting splits this IP range into smaller groups, called subnets.
A subnet mask then defines which part of the IP address identifies the subnet and which part identifies the individual device (also called the host). Routers use subnet masks to check if traffic is supposed to go to devices within the subnet or outside of it.
Why subnetting matters for secure network design
Subnetting helps to organize and protect a network by dividing it into smaller, controlled sections. This makes it possible to isolate areas that handle sensitive data and ensure only authorized users can access them. It also limits the impact of a compromised device or system.
Beyond security, subnetting also improves overall performance and simplifies troubleshooting. Smaller segments are easier to monitor, troubleshoot, and maintain, allowing IT teams to detect and fix problems more quickly.
IP addressing and subnet masks explained
To understand subnetting, you also need to understand how IP addresses and subnet masks work together. These elements determine where a device is on the network and how data moves between subnets.
How IP addresses are structured
Every IP address has two parts: the network ID and the host ID. The exact point where the address is divided depends on the subnet mask. This structure allows you to group devices logically within a network while still keeping each one uniquely identifiable.
There are also two versions of IP addresses: IPv4 and IPv6. An IPv4 address consists of four numbers (called octets) separated by dots, such as 192.168.4.28. An IPv6 address, on the other hand, contains eight groups of four hexadecimal digits separated by colons, such as 2001:0db8:85a3:0000:0000:8a2e:0370:7334.
What is a subnet mask?
In IPv4, a subnet mask is a 32-bit number that separates the network ID from the host ID in an IP address. Routers use subnet masks to determine if a device is on the same network or if data needs to be sent to another subnet. Common examples include 255.255.255.0, 255.255.0.0, and 255.255.255.192, each representing different network sizes.
For an in-depth understanding of how they work, you can read our full guide to subnet masks.
Network ID vs. host ID
Here’s how these terms differ:
- Network ID: Defines the network segment an IP address belongs to.
- Host ID: Refers to a specific device within that network.
As an example, let’s use 192.168.4.28 as the IP address and 255.255.255.0 as the subnet mask. The subnet mask tells us how many bits of the IP address are for the network and how many are for the host. In this situation, 192.168.4.0 would be the network ID and .28 would be the host ID.
The role of subnetting in cybersecurity
 Subnetting plays an important role in cybersecurity because it strengthens network defenses and limits potential attack paths. It also helps isolate valuable data and devices, playing a part in ensuring only authorized users can access them. However, subnetting requires strong security policies, strict access rules, and consistent monitoring to actually be effective.
Subnetting plays an important role in cybersecurity because it strengthens network defenses and limits potential attack paths. It also helps isolate valuable data and devices, playing a part in ensuring only authorized users can access them. However, subnetting requires strong security policies, strict access rules, and consistent monitoring to actually be effective.
How subnets reduce attack surfaces
An attack surface includes all potential entry points and vulnerabilities a cybercriminal can exploit. Subnetting helps reduce this surface by segmenting a network. If one subnet is compromised, attackers can’t immediately access every connected system.
This means that subnetting can reduce an attacker’s lateral movement, preventing them from moving deeper within a network. For example, even if a cybercriminal gains unauthorized access using a network security key, they can’t easily move between subnets without passing through routers and firewalls that enforce strict access rules and security policies.
Subnetting also improves threat monitoring, since security tools can focus on specific segments. This makes it easier to detect and respond to suspicious activity.
Isolating sensitive devices and internal traffic
Organizations can place servers that handle confidential information, like HR or financial data, in dedicated subnets to restrict access. They can also filter and log traffic between subnets to strengthen data protection and compliance with privacy regulations, like the General Data Protection Regulation (GDPR), for example.
In addition, businesses can set up separate subnets for guest traffic to make sure unmanaged devices can’t access the main company network.
Network access control with subnets
Network administrators can assign specific subnets to individual departments, like ensuring only payroll staff can access employee financial data. Grouping users and devices by subnet also makes it easier to manage and monitor permissions. In addition, IT security teams can further strengthen protection by allowing access to critical systems only from approved subnet IP ranges.
Common security risks in poorly configured subnets
Without strong security policies and proper network organization, subnetting can actually put data at risk instead of protecting it. Here are some common misconfigurations and associated risks to consider:
- Flat network design: A large subnet without further segmentation increases the attack surface and allows lateral movement if attackers gain unauthorized access.
- Subnet overlap: Two or more subnets using the same IP address range can cause routing errors and expose internal traffic, potentially leaking sensitive data.
- Lack of logging: If traffic between subnets isn’t properly monitored, it becomes difficult to detect suspicious activity or cross-segment cyberattacks.
- Poor isolation: Guest or Internet of Things (IoT) networks must be fully separated from subnets that host critical systems or data. Otherwise, attackers could exploit connected devices as entry points into the main network.
How subnets work with VPNs
Virtual private networks (VPNs) are often used on subnetted networks to enhance security and remote connectivity, but conflicts can occur if the network isn’t properly configured. This section focuses on business-grade VPNs; commercial VPNs typically don’t affect subnetted networks because they’re designed to avoid conflicts by using separate, large-scale IP address pools.
What happens when you use a VPN on a subnetted network
When you connect to a VPN, it assigns your device a virtual IP address from its own subnet (the VPN’s remote network). This new IP identifies your device on the VPN’s subnet, allowing it to communicate with other systems connected to the VPN. Your local IP address still exists, but it’s only used for communicating on your local subnet. This setup also helps prevent malicious third parties from tracing your real IP address or tracking network activity.
The VPN encrypts all data exchanged between your subnet and its servers, making it much harder for anyone to monitor or intercept it. All VPN-encrypted traffic is logically separated from your subnet’s internal communications and any external public traffic, ensuring data stays private and protected.
Split tunneling and subnet routing in VPNs
Split tunneling is a feature that lets you choose which traffic passes through the encrypted VPN tunnel and which data uses your local connection. Network administrators often configure it to optimize speeds and bandwidth usage or isolate sensitive subnets. For example, they might route all work-related traffic through the VPN, while allowing regular internet browsing to use the local connection.
VPN subnet conflicts and how to avoid them
VPN subnet conflicts happen when two or more networks use the same IP addresses. This can happen if a VPN’s subnet overlaps with a local department’s subnet (like HR, for example), or if two different VPN networks use the same IP range.
The easiest way to prevent conflicts is to make sure each subnet uses a unique IP address range. If that isn’t possible, Network Address Translation (NAT) can be configured to let devices on overlapping subnets communicate. However, NAT alone doesn’t fully solve the issue, and additional routing rules or port forwarding usually need to be set up so that traffic is directed to the correct devices across networks.
How to create and manage subnets
To create subnets, you first have to understand how IP addresses are allocated and organized using Classless Inter-Domain Routing (CIDR) notation. While subnets can be created manually, most network administrators use specialized tools to calculate, configure, and monitor them efficiently.
CIDR notation and address blocks
CIDR is the modern standard for allocating and organizing IP addresses. Introduced in 1993, it replaced the older IP classful addressing system (Classes A, B, C, D, and E). It’s used in both IPv4 and IPv6, with the latter using larger address blocks.
CIDR is more efficient because it allows IP address blocks of flexible sizes instead of fixed class boundaries, reducing wasted address space. It uses a slash followed by a number, called the prefix length, to indicate how many bits define the network portion of the address (for example, /24, /25, or /26).
CIDR notation also corresponds to subnet masks, showing how many addresses are available in each block. For instance, a prefix of /23 includes 512 addresses and uses 255.255.254.0 as a subnet mask, whereas a prefix of /24 has 256 addresses and 255.255.255.0 as a subnet mask. Most organizations that allocate IPs, such as internet registries, publish CIDR lists that show which address blocks are assigned to specific networks.
Step-by-step subnet calculation
Subnets are usually calculated using specialized tools because it’s faster and more accurate. That said, understanding how to calculate them helps you see how IPs are divided. Here’s a quick overview:
- Start with the base network address and its subnet mask. For this example, let’s use 192.168.3.0/24.
- Decide how many subnets you need based on departments, devices, or locations.
- Borrow bits from the host ID; each borrowed bit doubles the number of subnets but halves the number of available hosts. Our /24 example has 256 addresses. Borrowing one bit creates two /25 subnets, each with 128 addresses.
- Write down the new subnet masks. For /25, the new mask is 255.255.255.128.
- List the network and broadcast addresses, which are unusable. The network address is always the first one in the range, and the broadcast address is last. For example, the first subnet uses 192.168.3.0 as the network address and 192.168.3.127 for broadcasting.
- Note the range of usable hosts (the IPs that can be assigned to devices). In our example, the first subnet’s usable range is 192.168.3.1–192.168.3.126.
- Make sure each subnet’s IP range is unique to avoid any overlaps.
- Allocate the subnets logically, such as one per department or location.
Tools and scripts for subnet management
- Subnet calculators: Online apps that compute network, broadcast, and host ranges.
- Examples: IP Subnet Calculator, Calculator.net.
- IP address management services: Platforms that offer subnet visualization and troubleshoot connectivity issues.
- Examples: phpIPAM, SolarWinds.
- Command-line tools: Utilities that run in a command-line environment and provide quick network information or diagnostics.
- Examples: ipconfig, netstat, traceroute.
- Scripting tools: Scripts and libraries that manage subnets programmatically or automate subnet validation.
- Examples: Python, PowerShell.
- Monitoring platforms: Programs that track subnet usage, detect conflicts, and check overall network health.
- Examples: Nagios, Paessler PRTG.
Subnetting in IPv4 and IPv6
 IPv4 and IPv6 both use subnetting to organize and route network traffic, but they handle it differently. For example, each protocol uses its own address format. Also, IPv6 offers better flexibility and scalability, while IPv4 remains limited due to its smaller address space.
IPv4 and IPv6 both use subnetting to organize and route network traffic, but they handle it differently. For example, each protocol uses its own address format. Also, IPv6 offers better flexibility and scalability, while IPv4 remains limited due to its smaller address space.
IPv4 subnetting basics
IPv4 subnetting relies on CIDR and subnet masks, with its main goal being to manage address scarcity. Because IPv4 uses a 32-bit structure, it supports around 4.3 billion addresses. This limitation led to widespread use of subnetting and NAT to allocate and manage IP addresses efficiently. While IPv4 remains widely used today, global networks continue to transition to IPv6.
IPv6 subnetting and prefix length
IPv6 uses a 128-bit structure, providing an almost limitless pool of addresses (around 340 undecillion). Subnetting in IPv6 isn’t focused on saving address space but on creating a logical, hierarchical network design.
Like IPv4, IPv6 relies on CIDR, but replaces subnet masks with prefix lengths, where /64 is the standard for most subnets. Each /64 subnet includes over 18 quintillion addresses, ensuring every device has a globally unique IP and eliminating the need for NAT.
How IPv6 subnets enhance security and efficiency
IPv6 subnetting offers the following benefits:
- Improved isolation: Makes guessing IPs practically impossible due to the massive address space, reducing the attack surface even more.
- Native Internet Protocol Security (IPsec) support: Supports the IPsec protocol by default, which makes it easier to set up encrypted communications between subnets.
- Reduced broadcast traffic: Replaces broadcasts with multicast communication, limiting unnecessary traffic and reducing network congestion.
- Better traffic management: Makes it easier to enforce access rules, routing policies, and firewall restrictions based on prefix boundaries.
- Good scalability: Enables clean, hierarchical subnet design for enterprises and ISPs, simplifying future network expansion.
Common problems and best practices
 Poorly designed subnets can lead to performance problems, connectivity errors, and even security vulnerabilities. This section will discuss the most common issues that can occur and also outline some best practices for creating secure subnets.
Poorly designed subnets can lead to performance problems, connectivity errors, and even security vulnerabilities. This section will discuss the most common issues that can occur and also outline some best practices for creating secure subnets.
Misconfigured subnets and IP conflicts
Here are the most common subnet and IP address issues:
- Overlapping subnets: If two subnetworks use the same IP address range, it creates routing confusion and unreachable hosts. For example, if two locations use 192.168.3.0/24, routers won’t be able to distinguish between them.
- Duplicate IP addresses: The same IP can be assigned to two devices due to human error or Dynamic Host Configuration Protocol (DHCP) misconfigurations, causing connectivity issues or intermittent access.
- Incorrect subnet masks: If a device’s subnet mask doesn’t match the rest of the network, it can cause communication errors and IP configuration failures.
Best practices for secure subnet design
These are the best ways to secure subnets:
- Plan IP address schemes: Design a clear, hierarchical structure, and avoid reusing address ranges between locations or VPNs.
- Enforce access rules: Use routers and firewalls to make sure only authorized subnets can reach critical systems and resources.
- Combine virtual local area networks (VLANs) with subnets: Split the physical network into multiple VLANs and assign each one its own subnet to improve traffic isolation.
- Monitor subnet usage: Use IP and network monitoring tools to detect potential security issues, like unauthorized devices or suspicious routing behavior.
FAQ: Common questions about subnets
How many subnets are in a /24?
A /24 network has 256 total IP addresses. On its own, that’s one subnet with 254 usable hosts (because the first and last addresses are reserved for the network and broadcast addresses). If you divide it further, you can create up to 64 subnets (using /30), with each subnet containing four IP addresses. Out of these, only two addresses would be usable by devices, as the other two are the network and broadcast addresses.
How does subnetting improve network security?
Subnetting can strengthen network security because it divides a network into smaller segments that isolate valuable data and devices. This limits how much attackers can move around if they gain access to one part of the network. Administrators can also use subnets to control access to sensitive information, like only allowing HR staff to view employee contact information.
How do VPNs use subnets?
VPNs use subnets to manage and route encrypted network traffic. When you connect to a VPN, it assigns your device a virtual IP address from its own subnet that’s separate from your local network. This IP address helps the VPN server identify your device within its private network, allowing it to securely route data between your device and its subnet.
What’s the difference between a subnet, VPN, and VLAN?
A subnet is a logical division of an IP network that helps route traffic efficiently. A virtual private network (VPN) is a secure online service that changes your IP address and encrypts your web traffic, making your activity difficult to monitor. A virtual local area network (VLAN) is a logical segmentation of a physical network that separates devices on the same LAN or switch to improve organization and security.
Can subnets protect against cyberattacks?
Yes, because they reduce the attack surface by dividing a network into smaller, isolated segments. This makes it harder for cybercriminals to move through the network if they gain access to one area. It also helps IT security teams detect and contain threats more quickly, and it allows administrators to enforce access controls for sensitive data.
What is subnetting vs. supernetting?
While subnetting divides a large network into smaller segments, supernetting does the opposite. It combines multiple small networks into a single, larger one. Supernetting helps maximize the use of IP address space, which is especially important in IPv4 networks. It can also improve routing efficiency and decrease router overhead by minimizing the number of routes that need to be stored and managed.
Take the first step to protect yourself online. Try ExpressVPN risk-free.
Get ExpressVPN