Understanding the NIST Cybersecurity Framework: A comprehensive guide to CSF 2.0
While NIST’s Cybersecurity Framework (CSF) initially focused on critical infrastructure, the latest update makes it more applicable to all businesses, including smaller firms.
Although it’s not a mandatory regulation, many organizations adopt the framework to tailor their cybersecurity efforts to their unique needs, resources, and risks.
This post explains the framework, why it was created, and how the six core functions provide the structure for assessing and managing risks, as well as recovering from incidents.
What is the NIST CSF?
The CSF, created by the National Institute of Standards and Technology (NIST), is a voluntary framework consisting of cybersecurity risk management, standards, and guidelines.
It’s designed to help organizations better prioritize cybersecurity efforts, offering guidance on building appropriate solutions aligned with their unique priorities, assets, and risks.
The CSF serves as both a taxonomy and a mechanism for describing cybersecurity goals and posture. This makes universal communication easier, as organizations can describe their current and target cybersecurity posture in a consistent, structured way, even without a shared technical background or identical risk environments.
Which industries can benefit from the CSF?
The CSF can be helpful for all industries that rely on digital systems, data, or connected technology to operate. This includes critical infrastructure and supply chains, as well as smaller organizations such as retail, education, professional services, and nonprofits.
Any organization that handles sensitive information, financial data, or personal records may be vulnerable to cyberattacks and can find the CSF a helpful resource for understanding risk, strengthening security practices, and building a more resilient cybersecurity program.
The history of the NIST Cybersecurity Framework
The first version, CSF 1.0, was released in February 2014. Its purpose was to help organizations in sectors that support national and economic security identify, assess, and manage cyber risks more effectively.
While it was developed for high-risk sectors (such as energy, financial services, healthcare, and defense), it was voluntary and built to give organizations flexibility to adapt the framework to their specific needs.
What’s new in CSF 2.0?
In 2024, NIST released CSF 2.0, the first major structural update since its 2014 release. The new version expands the focus of the framework, making it applicable to all sectors and organizations worldwide, including small businesses, nonprofits, and schools.
The newer CSF 2.0 organizes cybersecurity as six high-level functions:
- Govern
- Identify
- Protect
- Detect
- Respond
- Recover
The update keeps the familiar structure of earlier versions but now includes a Govern Function that pulls together activities that were included in other functions or implied. This expanded the framework to emphasize governance, enterprise risk management, and broader organizational accountability for cybersecurity.
The 6 core functions of NIST CSF 2.0
From asset management and risk analysis to recovery planning and learning from incidents for continuous improvement, each of the six core functions addresses a portion of a cybersecurity strategy.
Although NIST doesn’t mandate any specific actions for organizations to take, it describes examples of activities organizations may consider for each function.
1. Govern
The newly added Govern Function focuses on how you set direction and accountability for cybersecurity across your organization. It helps you decide how cybersecurity supports your business goals, how much risk an organization is willing to tolerate, and who's responsible.
NIST describes the following actions for the Govern Function:
- Understand how risks can disrupt a business’s mission; the legal, regulatory, and contractual cybersecurity requirements; and who will be responsible for developing and executing the cybersecurity strategy.
- Assess the potential impact of total or partial loss of critical assets and operations; whether cybersecurity insurance is appropriate; risks posed by suppliers and other third parties.
- Prioritize managing cybersecurity risks alongside other business risks.
- Communicate policies alongside strategies for enforcement and maintenance, as well as leadership’s support.
As an example, if a business relies on suppliers or partners, it might use the Govern Function to set cybersecurity expectations, include security requirements in contracts, and involve partners in planning and response efforts.
2. Identify
The Identify Function focuses on developing a clear picture of your organization’s assets, system risks, data, and cybersecurity capabilities.
NIST suggests the following actions for the Identify Function:
- Understand what assets your business relies on, such as hardware, software, systems, and services.
- Assess assets for vulnerabilities and assess the cybersecurity program to identify areas of improvement.
- Prioritize inventorying and classifying data, and documenting threats using a risk register.
- Communicate plans, policies, and best practices to employees and any relevant third party, and communicate the importance of identifying improvements to processes and procedures to employees.
In practice, the Identify Function helps a business evaluate how it collects, uses, and stores data, including when third parties are involved, and helps prioritize a protection strategy for sensitive data. For instance, a manufacturing company might consider its product patent its most critical asset, or a retail company might prioritize customer payment data.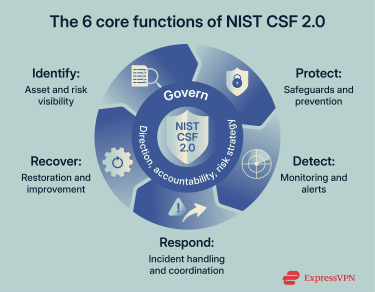
3. Protect
This function focuses on limiting the likelihood and impact of cyberattacks to help reduce downtime and damage and keep services running. It involves implementing safeguards to reduce exposure and lower the risk that a single incident causes serious harm.
NIST identifies the following actions for the Protect Function:
- Understand what information staff need to have access to and implement a policy of least privilege.
- Assess the quality and frequency of cybersecurity training.
- Prioritize protecting data and systems, such as by using strong authentication and credential practices, applying protective configurations, encrypting sensitive data, keeping systems up to date, and maintaining reliable backups.
- Communicate how to recognize common attacks, reporting procedures, and basic cyber hygiene measures.
As an example, an organization might use the Protect Function to focus safeguards on the systems and data most critical to its operations. This could include limiting access to sensitive systems based on job role, strengthening authentication and credential practices for key accounts, keeping devices and applications securely configured and up to date, protecting sensitive data wherever it is stored or transmitted, and ensuring backups are available and tested. Together, these measures help reduce exposure to common risks and limit the impact of incidents if they occur.
4. Detect
Early detection is critical, and the sooner your organization detects malicious activity, the easier it is to minimize potential damage. The Detect Function focuses on using procedures and technology that alert you to suspicious behavior.
NIST suggests the following actions for the Detect Function:
- Understand how to identify common red flags of a cybersecurity incident.
- Assess your technology and services for atypical behavior or signs of tampering.
- Prioritize detection tools, such as antivirus or anti-malware tools and monitoring services, to help identify suspicious activity on devices and networks.
- Communicate any relevant details to an incident responder.
As an example, an organization might use the Detect Function to define baseline activity for critical systems, monitor for deviations from that baseline, and ensure potential security events are reviewed and escalated so they can be addressed before causing wider disruption.
5. Respond
The Respond Function focuses on taking action once a cybersecurity incident has been detected. It addresses how an organization contains and manages incidents, coordinates response efforts, and communicates with relevant parties to limit harm and support recovery.
NIST describes the following actions for the Respond Function:
- Understand the incident response plan and who has the authority and responsibility for carrying out different aspects of the response.
- Assess the ability to respond to a cybersecurity incident and evaluate the incident to understand its severity, what occurred, and its potential impact.
- Prioritize taking steps to contain and address the incident to prevent further damage or spread.
- Communicate confirmed incident information to appropriate parties as required by laws, regulations, contracts, or policies.
As an example, an organization might use the Respond Function to activate its incident response plan, determine which teams or individuals need to be involved, take steps to contain the incident, and ensure required notifications and communications are carried out in a timely and coordinated manner.
6. Recover
The Recover Function focuses on restoring assets and operations that were affected by a cybersecurity incident. It addresses how an organization returns to normal operations, communicates recovery progress, and applies lessons learned to improve resilience over time.
NIST highlights the following actions for the Recover Function:
- Understand who has responsibility for recovery efforts and decision-making.
- Assess what happened during the incident by reviewing response and recovery actions taken, documenting lessons learned, and evaluating the integrity of backed-up data and assets before restoration.
- Prioritize recovery actions based on organizational needs, available resources, and the systems, data, or services that were impacted.
- Communicate regularly and securely with internal and external stakeholders about recovery progress, and document the completion of recovery activities and the resumption of normal operations.
As an example, an organization might use the Recover Function to coordinate restoration efforts across teams, verify that systems and data are ready to be brought back online, communicate status updates to stakeholders, and capture lessons from the incident to strengthen future recovery planning.
How to implement the NIST CSF
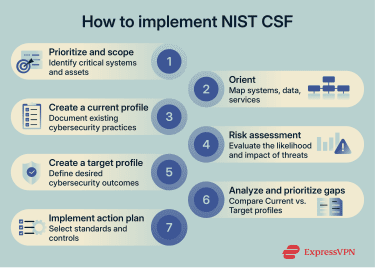 NIST outlines a seven-step approach for organizations to start applying the CSF. Here’s what it looks like:
NIST outlines a seven-step approach for organizations to start applying the CSF. Here’s what it looks like:
- Prioritize and scope: Identify which systems and assets are most critical from a cybersecurity perspective.
- Orient: Focus on the systems, data, and services that support your priorities. Consider regulatory and legal requirements, your organization’s overall approach to risk, and known threats or common vulnerabilities.
- Create a Current Profile: Document your existing cybersecurity practices and outcomes. This highlights what's already in place and where coverage is incomplete, creating a clear baseline for improvement.
- Conduct a risk assessment: Use your Current Profile as a foundation, incorporating updated intelligence to evaluate the likelihood and potential impact of cybersecurity events.
- Create a Target Profile: Define the cybersecurity outcomes you aim to achieve. Shape this future state based on business needs, risk tolerance, and expectations from customers, partners, or regulators.
- Analyze and prioritize gaps: Compare the Current Profile with the Target Profile to identify gaps, then prioritize them based on risk, cost, and business impact.
- Implement the action plan: Address the gaps between these profiles to progress toward your target security posture. Choose the standards, guidelines, and security practices that best fit your risk environment and operational needs.
Key resources and tools
The NIST provides several free resources to help you get started:
- CSF 2.0 Core Document: The full framework document outlines the six functions, including categories, subcategories, and structure.
- CSF 2.0 Reference Tool: This interactive online tool lets you search, filter, and export CSF Core elements (functions, subcategories, and implementation examples).
- Quick-Start Guide: This small business guide prioritizes steps for companies with limited resources.
FAQ: Common questions about the NIST Cybersecurity Framework
What is the NIST Cybersecurity Framework?
The National Institute of Standards and Technology (NIST) Cybersecurity Framework (CSF) is a voluntary collection of guidelines, best practices, and standards designed to help organizations handle cybersecurity more effectively based on their unique assets, threats, and risk tolerance.
What are the 6 components of the NIST Cybersecurity Framework?
The six core functions of the National Institute of Standards and Technology (NIST) Cybersecurity Framework (CSF) are: Govern, Identify, Protect, Detect, Respond, and Recover.
How to implement the NIST CSF?
Implementing the National Institute of Standards and Technology (NIST) Cybersecurity Framework (CSF) starts with defining your organization's objectives. Next, outline assets, potential threats, and vulnerabilities. You can then document your current practices in a Current Profile, define a Target Profile that reflects the outcomes you want, and address the gap between the two profiles.
Why is the NIST CSF important?
The National Institute of Standards and Technology (NIST) Cybersecurity Framework (CSF) is important because it provides a structured, flexible approach that helps organizations reduce risk, improve resilience, and respond more effectively to cybersecurity incidents.
How can small businesses benefit from the NIST CSF?
The National Institute of Standards and Technology (NIST) Cybersecurity Framework (CSF) provides flexible guidance to small businesses for identifying risks and building resilience, without complex processes. It helps them assess their assets and prioritize protection, detect threats quickly, respond effectively to incidents, and recover faster from cyberattacks.
What resources are available for organizations using the NIST CSF?
The National Institute of Standards and Technology (NIST) offers free resources, including documents that explain the framework, a Reference Tool to help explore specific elements, and Quick Start Guides that provide practical guidance. When time or resources are limited, the Small Business Quick Start Guide is often the easiest place to begin.
Take the first step to protect yourself online. Try ExpressVPN risk-free.
Get ExpressVPN