Unraveling ATM jackpotting: What you should know
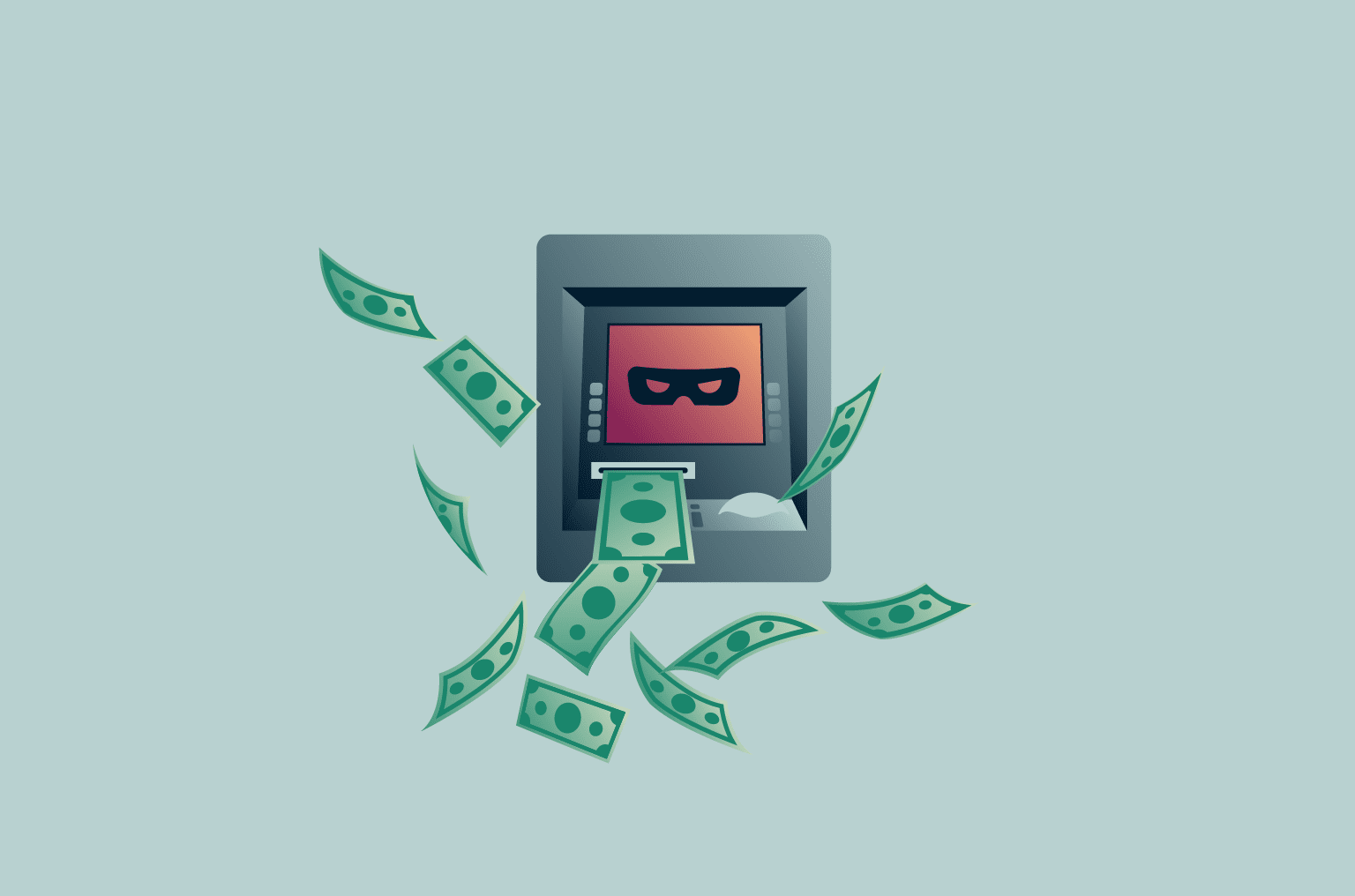
In an ATM jackpotting attack, instead of stealing card details, attackers target the ATM itself, often using malware or unauthorized access to internal systems.
In this article, we’ll explain how jackpotting works, describe some prevention measures, and share some practical tips for everyday ATM users.
What is ATM jackpotting, and how does it work?
During an ATM jackpotting attack, criminals force an ATM, a machine that’s generally perceived as reliable and safe, to dispense cash on command using malware or direct hardware manipulation.
Common ATM jackpotting techniques
ATM jackpotting attacks can be carried out in several ways, but two techniques are the most common: malware-based attacks and black-box attacks.
Malware-based attacks
In malware-based ATM jackpotting attacks, criminals take advantage of weak physical security to get unauthorized access to the ATM itself.
Once inside, attackers deploy malware that interferes with the ATM’s normal operation and takes control of the cash-dispensing system. To avoid raising suspicion, they may pretend to be legitimate technicians or blend into places where maintenance work wouldn’t look out of place. If the attack works, the ATM can be forced to release large amounts of cash in a short time, sometimes until it runs out completely.
Different strains of jackpotting malware work in different ways. Well-known examples include Ploutus, Cutlet Maker, and Tyupkin. Some variants are activated directly at the machine, while others rely on indirect or external triggers. What they all have in common is that they combine physical access with malicious software to manipulate the ATM itself.
Black box attacks
In black box jackpotting, attackers connect a separate device that takes direct control of the cash dispenser hardware. It still starts with physical access, but once connected, the black box acts like a counterfeit controller that can send dispense commands, sometimes controlled remotely over a wireless link. Black box attacks are known for speed and discretion, with reports of ATMs being emptied in under 10 minutes.
After the theft, the device is removed and the cables are reconnected, but while the ATM may appear operational, it has been physically compromised and requires inspection.
How ATM jackpotting affects everyday users
At first glance, ATM jackpotting looks like a bank-only problem because the cash comes from the machine, not straight from a user’s account. However, everyday users are still affected by this threat.
For example, if an ATM gets jackpotted, it can run out of cash or go out of service afterward, sometimes with a generic “Out of Order” message. That is more than a minor inconvenience if it’s the only machine nearby, or if you need cash quickly and your routine option suddenly goes dry.
Cash-out attacks are also expensive, with reported losses reaching tens of thousands of dollars in a short window. Over time, operators may respond by reducing cash levels, pulling higher-risk machines, or investing in upgrades like locks and alarms. This might result in higher fees and fewer convenient locations for users.
Signs an ATM might be vulnerable
Attackers tend to pick ATMs that let them work quickly and quietly, with fewer hurdles if something goes wrong.
Identifying high-risk ATMs
There are multiple aspects that can make an ATM attractive to criminals. That’s why, for banks and financial institutions, layered controls matter, and multiple protections need to be put in place.
Jackpotting attackers tend to pick machines that are easier to access without interruption and more likely to have gaps, such as outdated software that no longer gets security updates or older configurations that are harder to lock down. Alarms, camera coverage, and software updates can help to resolve these issues.
Warning signs that an ATM may be compromised
Jackpotting isn’t always apparent in the moment, but there are subtle red flags to watch for.
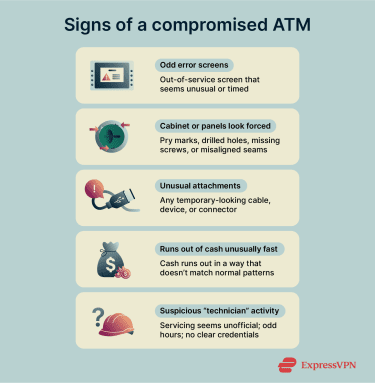
- “Out of service” or odd error screens: Sometimes an ATM is genuinely down. But in jackpotting incidents, machines can be made to look out of order while they’re being controlled.
- Signs the cabinet or panels were forced: Watch for pry marks, drilled holes, missing screws, misaligned panels, or fresh damage around seams. A compromised machine may appear “clean” at the card slot because access is often through the service area rather than the card slot.
- Unusual attachments, cables, or devices: If you notice a cord coming from the machine, a USB device, or anything that appears to be temporarily connected, don’t use that ATM. Step away and report it to the bank.
- Repeated “out of cash” problems: One empty ATM doesn’t prove anything. But if it keeps running out of cash unusually quickly compared to its usual refill pattern, it could be a sign that something isn’t right.
- Suspicious “technician” activity: In real cases, criminals have posed as maintenance staff to buy time. If someone is inside an ATM at an odd hour and it doesn’t look official, don’t confront them. It is best to leave and notify the bank or local authorities.
 If anything feels off, trust that instinct. Find another ATM, and consider using one inside a bank branch or a well-monitored area when you have the option.
If anything feels off, trust that instinct. Find another ATM, and consider using one inside a bank branch or a well-monitored area when you have the option.
Real-world examples of ATM jackpotting
Here are a few notable real-world examples and cases that illustrate the ATM jackpotting threat.
Barnaby Jack’s demonstration (Las Vegas, 2010)
In 2010, security researcher Barnaby Jack demonstrated ATM jackpotting, showing that ATMs could be made to dispense cash on command, including a remote scenario and another requiring hands-on access to the machine.
The ATM even displayed “Jackpot!” during the demo, which helped cement the term “ATM jackpotting” in public discussions.
Ploutus malware (mid-2010s)
After early demonstrations gained widespread attention, real malware families targeting ATMs emerged, such as Ploutus, which was first detected by cybersecurity company Symantec in 2013. These malware strains were adapted to specific ATM models and used in criminal operations, signaling a shift toward repeatable tooling for jackpotting-style attacks.
Tyupkin targets ATMs (2014 onward)
Malware like Tyupkin (also reported as Padpin) was documented controlling ATMs through software installations that could be triggered via secret PIN pad sequences, allowing thieves to dispense cash without a card.
U.S. Secret Service alerts (2018 onward)
The U.S. Secret Service has warned about sophisticated ATM jackpotting attacks since at least 2018, describing how physical access to install malware or hardware can lead to rapid, unauthorized cash dispensing at stand-alone machines.
U.S. jackpotting incidents (2025)
There have been multiple documented jackpotting-style thefts in 2025:
- Salina and Wichita, Kansas: Police investigated multiple jackpotting attacks where suspects used malware or related techniques to cause ATMs to dispense cash unlawfully at multiple locations.
- Illinois jackpotting arrests: Three men were charged in an ATM jackpotting scheme in Edwardsville, Illinois, after attempting to access an ATM’s control panel and install software to manipulate the machine.
- Northern Virginia: Police in Fairfax County sought help identifying suspects after about $175,000 was stolen from an ATM using a jackpotting method. Surveillance footage showed individuals accessing the machine and withdrawing cash without a card or a normal transaction.
- Bay Area jackpotting arrests: Three people were charged in Ukiah, California, after allegedly installing devices inside ATMs and triggering cash withdrawals.
How to protect ATMs from jackpotting
The sections below outline how banks, credit unions, and ATM operators approach financial institution security. Because ATM jackpotting attacks can involve a mix of physical access, software weaknesses, and network exposure, defenses are usually built in layers rather than relying on a single control.
Preventive measures for financial institutions
These measures focus on protecting the ATM from physical access and local software compromise. Since many jackpotting incidents begin with unauthorized physical access, improving physical controls should be addressed first.
Key areas typically include replacing shared cabinet keys with high-security locks and enforcing stricter key control. Anti-tamper protections can help prevent silent cabinet access. Door sensors, vibration sensors, alarms, and cameras are commonly used to reduce the time available to attackers and increase the likelihood of detection.
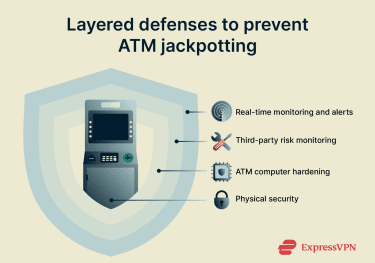 The ATM computer itself should also be hardened. This generally involves keeping software and firmware up to date to reduce exposure to known operating system vulnerabilities, changing default passwords, and restricting USB port functionality. Because legitimate servicing may require USB access, this control often needs careful configuration. Additional safeguards may include enabling full-disk encryption and secure boot, using application allowlisting to prevent unauthorized code execution, and disabling unused ports and autorun features.
The ATM computer itself should also be hardened. This generally involves keeping software and firmware up to date to reduce exposure to known operating system vulnerabilities, changing default passwords, and restricting USB port functionality. Because legitimate servicing may require USB access, this control often needs careful configuration. Additional safeguards may include enabling full-disk encryption and secure boot, using application allowlisting to prevent unauthorized code execution, and disabling unused ports and autorun features.
Third-party risks should be addressed as well. When vendors are involved in maintenance, monitoring, or cash handling, it’s important to clearly define responsibility for each control and verify that those controls are in place. Contracts and audits can be used to enforce patch timelines, technician access should be verified and logged, and escalation procedures should be established to avoid gaps during handoffs.
Finally, prevention should be paired with timely detection. ATM-specific monitoring can help identify unexpected “out of service” states, reboots, or off-hours downtime, allowing teams to investigate quickly and limit potential losses.
Strengthening ATM network security
Device-level hardening is important, but it is not sufficient on its own. An ATM can still be exposed if the network it relies on is weak. For this reason, ATM networks should be treated as high-risk environments with tightly defined boundaries and layered controls:
- Secure ATM communications: ATM-to-host traffic should be encrypted and authenticated using virtual private networks (VPNs) or equivalent secure tunnels, combined with strong endpoint authentication and network segmentation. This helps reduce the risk of message interception, spoofing, and man-in-the-middle (MITM) attacks caused by weak or exposed configurations.
- Network segmentation and access control: ATM infrastructure should be isolated from the broader enterprise network, with strict firewall rules and allowlisted endpoints used to limit access. Approved routes and service paths should be monitored to detect unexpected connections or configuration changes.
- Remote access protection: Administrative access should be protected with multi-factor authentication (MFA), default credentials should be removed, and access should be restricted based on role, device, and geographic location.
- Network-level detection and containment: Monitoring should focus on identifying abnormal patterns such as repeated service-mode events, unexplained offline status, or dispensing activity that does not align with transaction records. Environments should also support isolating a single ATM quickly without disrupting the wider fleet.
Incident response best practices
Even with layered defenses, an ATM jackpotting attempt can still slip through. The practices below focus on fast containment, evidence preservation, and safe recovery to prevent a single incident from becoming a wider cash-out event.
- Disable the ATM quickly (if safe and authorized): If monitoring or staff reports indicate an active cash-out, the ATM should be taken out of service and dispensing should be stopped as quickly as policy allows. Authorization requirements and the exact meaning of “disable” should be clearly defined in advance.
- Treat the site as a crime scene: Secure the area and avoid touching the cabinet, ports, or any suspicious attachments. Preserve the exact state for forensic review.
- Notify law enforcement early: Escalate through the appropriate local and federal channels when fraud is suspected, especially if the pattern suggests coordinated cash-out activity.
- Preserve logs and video immediately: Pull dispenser logs, event logs, remote management logs, and relevant CCTV footage before retention cycles overwrite it. Maintain a chain of custody for anything collected.
- Contain the threat across the fleet: Assume the same crew may be hitting multiple machines. Push rapid internal alerts, increase monitoring, and consider temporary regional actions where risk is elevated.
- Eradicate and recover safely: Reimage affected systems, rotate keys and credentials, patch and harden the weakness that enabled the compromise, then validate before returning the ATM to service.
- Document and improve: Capture timeline, detection gaps, response latency, and control failures. Feed those lessons into updated process documentation, training, and drills.
How users can protect themselves at the ATM
ATM jackpotting is mainly a bank problem, but you can still lower your odds of running into a compromised machine. A lot of this advice is also relevant for avoiding skimming and other ATM fraud.
- Use ATMs in well-lit, well-monitored spots, like bank branches or busy areas.
- Give the machine a quick look. If panels seem loose, damaged, or forced, skip it.
- Walk away if it’s “Out of Service,” stuck on errors, or acting strangely.
- Stay aware of people nearby. If someone’s hovering or “servicing” it at odd hours, don’t engage them directly, but report the situation to the bank.
- Cover your PIN and take your cash fast. Jackpotting doesn’t need your PIN, but other scams do.
- When practical, use contactless or digital payments (prefer safe online payment methods) instead of extra cash withdrawals.
Common myths around ATM jackpotting
Here are some of the top myths that come up about ATM jackpotting and what the truth behind them really is.
Myth: ATM jackpotting is the same as skimming
Skimming is built around stealing card data and PINs so criminals can clone cards or commit fraud later. Jackpotting is different; it focuses on making the machine dispense cash by abusing the ATM’s internal systems, so the payout happens right then and there.
These two crimes can happen in the same kind of locations, but they target different things. Skimming targets customer data, while jackpotting targets the ATM’s cash supply.
Myth: ATM jackpotting always uses MITM attacks
Most jackpotting cases don’t start with a remote attacker intercepting network traffic. The more typical pattern involves hands-on access, then malware or a device that can send unauthorized commands to the dispenser. That said, there have been alerts about MITM techniques tied to jackpotting attempts. However, it’s not the primary method used in jackpotting.
Myth: Only old ATMs are vulnerable
Older ATMs are often easier targets because legacy systems and weaker controls are more common than they are in newer machines. However, “new” doesn’t automatically mean “safe.” Security posture matters more than age; if access controls are weak, defaults are left in place, ports are exposed, or monitoring is thin, even a newer machine can be at risk.
A practical way to think about it is this: aging hardware and outdated software can increase risk, but configuration, patching, and physical security are the real deciders on whether an ATM is a soft target.
FAQ: Common questions about ATM jackpotting
How can users avoid ATM skimming and jackpotting risks?
Follow ATM safety tips, such as using ATMs in well-lit, busy areas, ideally inside bank branches. Give the machine a quick look before you use it, and walk away if anything seems off. Keep your PIN covered and turn on bank alerts.
How can banks better protect ATMs against jackpotting attacks?
Layered ATM defense is important so one missed control doesn’t lead to a cash-out. Tight operational controls also matter, like key management, technician verification, and rapid response when a machine goes offline unexpectedly.
What steps should be taken once an ATM jackpotting attempt is suspected?
Treat the site as a crime scene, notify law enforcement, and alert internal teams so nearby machines can be checked fast. Officials should follow incident response practices and take the ATM out of service. Only return the ATM to service after it’s been reimaged, patched, and the entry point has been fixed.
What security measures prevent malware-based jackpotting?
The strongest approach is physical access controls, plus software controls that stop unknown code from running. Full-disk encryption, secure boot, and application allowlisting make it harder to install or execute malware, even if someone gets inside the cabinet.
Take the first step to protect yourself online. Try ExpressVPN risk-free.
Get ExpressVPN