Insider threats: Understanding, prevention, and management


Cybersecurity strategies and solutions often focus on external threats, like malicious third parties and hacker groups targeting a network or organization. But dangers don’t always come from the outside; insider threats can be just as dangerous.
This article will explain what an insider threat is, what common red flags are, and what organizations can do to mitigate the risks of insider threats.
What are insider threats?
Insider threats are security risks within an organization that stem from people with authorized access who abuse or misuse that access, either deliberately or accidentally. Anyone who has or had internal access to company files and systems, and whose actions or mistakes put the organization at risk from within, could be an insider threat.
This means an insider isn’t limited to employees only; it can include contractors, vendors, business partners, consultants, or anyone the organization has given access or sensitive information to. What makes them a threat is that they understand and can use internal access in ways that put the organization’s mission, people, or assets at risk.
Examples of insider threats and harm
Examples of ways in which insider threats manifest and the types of damage they can do include:
- Employees storing company data on personal or unsecured devices, which increases the risk of data exposure.
- Employees taking proprietary information before leaving the organization.
- External attackers using stolen employee credentials to access internal systems under the guise of legitimate users.
- Insiders stealing and sharing trade secrets with rival firms for personal or financial gain.
- Users abusing their access privileges to delete corporate data or exfiltrate customer information.
Why insider threats are hard to detect
The access privileges afforded to insiders make insider threats especially difficult to detect because their actions often look like normal, authorized behavior rather than suspicious activity.
An employee accessing a database of sensitive customer data, for example, might simply be carrying out their usual duties, but could also be planning to share or leak that same data. Similarly, a worker connecting a USB drive to their computer might simply need to transfer some files, but could also be infecting the office network with a virus.
Insiders may also act slowly and incrementally to avoid drawing attention. Organizational trust bias further complicates detection, as teams tend to assume good intent and hesitate to question legitimate users, especially those with elevated privileges. As a result, insider threats can go unnoticed for extended periods of time.
Types of insider threats
Insider threats can be classified into various categories depending on the intentions and identities of those involved.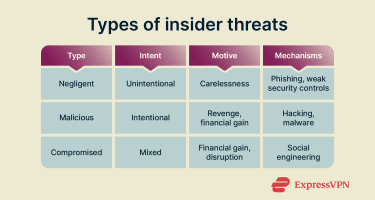
Negligent insider threats
Negligent insider threats create security risks through carelessness or lack of awareness. This can include falling for phishing attacks, reusing weak passwords, bypassing security controls to save time, or mishandling sensitive data. Common scenarios include losing an unencrypted laptop, uploading files to unauthorized cloud services, or mistakenly emailing confidential information to the wrong recipient.
Malicious insider threats
Malicious insiders intentionally misuse their authorized access to harm the organization under its digital defenses radar. Because they already understand internal systems and processes, they can steal data, sabotage systems, or leak sensitive information while avoiding immediate detection.
Compromised insider threats
These types of threats arise when external attackers gain control of legitimate user credentials. Although the attacker is external, the risk comes from the inside as the organization continues to treat the access as trusted and authorized. These threats typically stem from stolen credentials obtained through phishing, social engineering, or credential reuse from prior breaches, all of which allow attackers to blend in with normal activity.
How insider threats work
Insider threats can work in very different ways, depending on their nature and intent. A targeted, malicious attack, for example, may involve stages of planning, sabotage, and even attackers attempting to cover up their activities. An unintentional threat, meanwhile, may simply make a mistake one day, triggering a sequence of events that damages their company.
While the exact mechanisms vary, all of these attacks share one important feature in common: misuse of insider privileges.
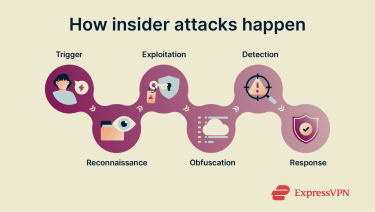
The insider threat lifecycle
Insider threats don’t always follow a fixed, familiar pattern, but they typically include some or all of the following stages:
- Trigger: This is the inciting incident that leads to the attack taking place. It might be a lack of training, in the case of negligent insider threats, or a workplace conflict that causes an employee to become angry and resentful.
- Reconnaissance: This is when the insider begins planning out their attack, identifying the data they want to steal or the devices and systems they intend to target.
- Exploitation: At this stage, the insider threat manifests in the form of data exfiltration, system manipulation, unauthorized access, or malware infection.
- Obfuscation: During this phase, the insider may take measures to cover their tracks, which may include deleting logs or manipulating data.
- Detection: Provided the company has adequate security and monitoring tools in place, they should, at some stage, detect that an attack has occurred.
- Response: The affected company will then need to issue a response, which may include terminating the offender, pursuing legal action, informing the authorities, and auditing their cybersecurity policies.
Common motivations behind insider threats
Insiders who intentionally carry out attacks from within may have numerous motivations behind their actions. These include:
- Financial gain: Insiders may seek profit by selling sensitive data, trade secrets, or access to internal systems.
- Resentment or revenge: Feelings of unfair treatment, lack of recognition, or conflict at work can drive intentional misuse of access.
- Job insecurity or personal stress: Organizational changes, layoffs, or personal financial pressure can increase insider risk.
- Coercion or blackmail: External actors may pressure insiders into abusing their access through threats or manipulation.
- Carelessness or low awareness: Unintentional threats often result from inattention, fatigue, or poor understanding of security practices.
- Disengagement or convenience: Employees may bypass policies to save time or simplify tasks, unintentionally creating risk.
Some attackers may even be coerced or blackmailed into committing attacks by external parties. Meanwhile, those involved in unintentional attacks may simply be acting out of carelessness or disengagement with their duties. Understanding the varying motivational and emotional factors at play can help businesses spot and prevent insider threats.
Signs to help identify insider threats
Insider threats can be more difficult to spot and react to than external ones, and the red flags for insider threats could have benign explanations. When assessing a situation, it’s important to also look at patterns and context. Here are some of the warning signs businesses and IT administrators can watch out for:
Unusual behavior patterns
While their duties may vary, many employees will often follow familiar patterns or routines during a typical working day. If they start to deviate from those patterns or behave in suspicious ways, that could indicate a threat. Suspicious behaviors may include:
- Logging onto work systems at non-working hours or from unusual locations.
- Accessing applications or files they don’t usually need or that aren’t related to their role.
- Attempting to bypass security controls.
- Sudden spikes in activity, like bulk file downloads.
Suspicious data access and movement
Employees naturally need to access various files and folders each day, but there’s a difference between normal and suspicious data interactions. If employees suddenly save or transfer large amounts of sensitive information, for example, that could be a red flag. Other suspicious signs include unusual data transfers just before an employee is due to leave a company, or attempts to access or move confidential files to personal devices or cloud storage services.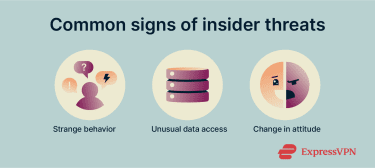
Change in employee attitudes or work habits
This relates mainly to intentional and malicious insider threats, rather than negligent ones. If workers are actively plotting to attack or damage an organization from inside, there may be clear human, emotional signs of that intent. They might seem frustrated, stressed, or disengaged, for example, or demonstrate recurring bad habits, like ignoring security protocols.
Why insider threats matter
Data breaches and their implications
While external parties have to break through various barriers and defenses to access company files and data, insiders often already have a certain level of access. They can download, save, and share important information, either intentionally or inadvertently, potentially triggering leaks of customer details or other data.
The implications of this can impact a business both financially and reputationally. According to IBM’s Cost of a Data Breach report, some of the most costly data breaches in 2025 were those with an initial insider threat vector.
Companies may also face legal challenges and reputational damage if they allow sensitive data to leak. Customers, too, can be affected if their personal information gets shared with third parties or sold.
Financial and legal consequences
The financial and legal complications that can stem from insider attacks are difficult to calculate because the impact depends on the scale of the attack. In a worst-case scenario, companies could lose invaluable trade secrets or face large-scale lawsuits if an insider leaks sensitive user data.
Long-term reputational damage
Organizations that fall victim to insider attacks are often seen as less trustworthy by partners and customers. This can have a negative impact on revenue and profits, potentially causing even major companies to lose some of their market share and paving the way for their rivals to overtake them. It can take a long time to build back trust following an incident like this.
Real-world examples of insider threats
Organizations can also look to the past, exploring how real-world instances of insider attacks unfolded. Well-known examples include:
- Theft of proprietary data by departing employees: Investigations have shown cases where employees with access to sensitive intellectual property copied large volumes of internal files before leaving an organization, later using or sharing that information with competitors.
- Credential compromise through social engineering: Some incidents have involved attackers tricking employees into revealing login credentials through phishing or voice-based scams. Once obtained, these credentials allowed attackers to access internal systems and customer data while appearing as legitimate users.
- Abuse of trusted cloud or infrastructure access: Reports have documented situations where individuals with deep technical knowledge exploited misconfigurations or privileged access to reach sensitive databases, exposing large volumes of customer information.
- Long-term espionage by trusted insiders: Some insider threat cases involve individuals who quietly exfiltrated sensitive information over many years on behalf of foreign governments or competitors, causing sustained national security and economic damage.
- Accidental data loss caused by internal error: Media reports have also highlighted incidents where employees accidentally deleted or damaged critical systems or datasets by failing to follow established procedures, resulting in permanent data loss and service disruption.
How to mitigate the risk of insider threats
As well as monitoring for signs of insider attacks, organizations can also deploy various security tools and strategies to minimize their risks.
Access control and least privilege
Access control is about restricting what files people can access, ensuring that they only have access to the data they need to carry out their duties. When implemented correctly, it helps to reduce the attack surface, as even if an employee is compromised or makes a mistake, they won’t be able to do as much damage by leaking or stealing vast amounts of data.
Offboarding and role-change management
Insider risk often increases during employee departures or role transitions. Promptly revoking access, recovering devices, and reviewing recent activity during offboarding helps prevent misuse of data after roles change or employment ends.
Employee training and security awareness programs
Many insider attacks happen because of mistakes, with workers simply clicking the wrong link or failing to follow safe data practices. This can be remedied with education.
Organizations should regularly carry out security awareness training to help staff understand how to carry out their duties safely and help staff members recognize and report insider threats. Training should also be ongoing and, if possible, role-specific, so that employees understand how insider threats relate directly to their day-to-day responsibilities.
User behavior analytics and monitoring
Analytics tools can track how users behave, monitoring their actions in real-time. They can establish baseline patterns of normal user activity, which makes it easier to spot when someone breaks those patterns and acts in unexpected or suspicious ways. If a user logs in at unusual times or tries accessing files they don’t usually access, for example, analytics tools can spot that and flag it, alerting the relevant teams to take action quickly.
Zero-trust and continuous verification
Zero-trust security works on the principle that no user or device should be automatically trusted, regardless of their experience or seniority. Every single access request should, instead, undergo continuous verification checks. In conjunction with other tools, like behavioral analysis and access controls, this can reduce the risk of insider attacks causing serious harm.
FAQ: Common questions about insider threats
What is an example of an insider threat?
An example of an insider threat could be a disgruntled employee who decides to intentionally leak sensitive business information or exploit their insider access to install malicious software on business devices. There are also cases of unintentional insider threats, where internal parties make mistakes that lead to data losses, leaks, or malware infections.
What are the types of insider threats?
Insider threats generally fall into three categories: negligent, malicious, and compromised. Negligent threats and compromised threats are, for the most part, unintentional. While malicious threats include an individual who purposely aimed to harm an organization from within.
How can organizations detect insider threats early?
Organizations can use various security systems and tools to look for the signs of insider threats and attacks. They can carry out audits of their security systems and access controls, for example, use behavioral analysis tools to spot suspicious activity or changes in behavior, and establish clear incident response plans to take action if and when an attack is detected.
Are inside threats more dangerous than external attacks?
Not always, but they certainly can be. This is partly because insiders already have certain levels of access to sensitive data and files and their attacks are often harder to detect and prevent.
How do remote and hybrid work environments increase insider risk?
Remote and hybrid workers may access sensitive company files and applications from their own home devices and remote networks, which are challenging for business IT teams to manage and secure. They might also use unapproved applications and lack the same oversight as in-office workers. All of this increases the attack surface and risk of mistakes being made and data being leaked or lost.
Take the first step to protect yourself online. Try ExpressVPN risk-free.
Get ExpressVPN