Types of cyber insurance: Coverage options explained
Cyberattacks and data incidents can affect any organization, not just large companies. Cyber insurance can help cover certain costs; however, the right coverage varies by business size, industry, and how the business handles sensitive data and online systems.
Understanding the main types of cyber insurance and common add-ons helps clarify what a policy can (and cannot) do. This article breaks down the major coverage types, how they differ, and when specialized policies may be a better fit.
Please note: This information is for general educational purposes and not financial or legal advice.
What is cyber insurance for businesses?
Cyber insurance for businesses is a form of digital risk protection. It can help organizations manage the financial impact of cybersecurity incidents, such as internal errors, system failures, data breaches, and malware attacks. These losses can be extensive, often including investigation and recovery costs, legal support, notification expenses, and certain regulatory or compliance-related costs, depending on the policy.
For example, the FBI 2024 Internet Crime Report lists $2.77 billion in reported losses tied to business email compromise (BEC), making it the second-highest loss category in that report (after investment fraud).
Sophos, a cybersecurity company, reported a median ransom payment of about $2 million among organizations that paid in its recent ransomware survey.
Costs also vary by industry. IBM reported that the financial industry averaged $5.56 million per data breach in 2025, about 26% higher than the global average.
Learn more: Read our detailed report on the true cost of cyberattacks.
Core categories of cyber insurance coverage
Comprehensive cyber insurance policies are usually structured around two main coverage categories: first-party coverage for the business’s own losses and third-party coverage for liability claims made by others. Some insurers also offer additional liability coverage, either as endorsements within a cyber policy or as separate policies, depending on the business and insurer.
First-party cyber insurance coverage
First-party cyber coverage addresses losses that affect a business directly. Many policies include breach or incident response costs associated with unintended data exposure, such as forensic investigation, legal support, notification-related expenses, and crisis communications.
In addition, first-party coverage often addresses operational disruption (business interruption) and may also cover digital data recovery or restoration costs, such as restoring or replacing damaged data or software, depending on policy wording.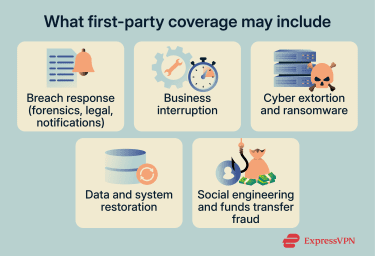
Cyber extortion and ransomware coverage can also fall under first-party protections, but terms vary widely. Some policies include expenses such as negotiation support and incident response services and may cover extortion payments in some cases, typically subject to conditions, sub-limits, and legal/compliance constraints.
Social engineering and cyber fraud-related losses (including some fund transfer or fraudulent instruction scenarios) may be offered in certain forms of endorsements, but availability and definitions differ substantially across insurers and policies.
Coverage varies by policy. Many include core breach response costs, while business interruption and extortion-related coverage are commonly subject to exclusions, waiting periods, sub-limits, or optional endorsements.
Third-party cyber insurance coverage
Third-party cyber liability insurance may respond to claims brought by parties outside the business, like customers, clients, suppliers, or regulators. These policies typically focus on liability arising from security and privacy incidents and may include legal defense and settlement costs for covered claims.
They may also address liability tied to unauthorized access, disclosure, or misuse of data and network security failures that cause harm to others, for example, malware transmission or denial-of-service (DoS) events.
Regulatory coverage varies. Some policies may cover certain regulatory defense costs, while coverage for fines or penalties may be limited, excluded, or available only where such amounts are legally insurable in the relevant jurisdiction.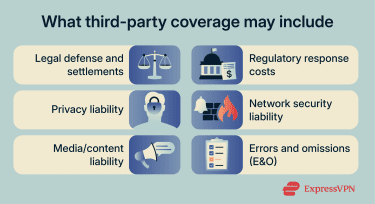
Specialized types of cyber insurance
Beyond core cyber coverage, many insurers offer options for more specialized risks. Because these risks can overlap with crime, property/technology, or professional liability insurance, they are often provided through endorsements or separate coverage grants rather than the default core package.
Social engineering and funds transfer fraud coverage
Funds transfer fraud (FTF) refers to scams where criminals use phishing or other social engineering to trick authorized users into sending money to the wrong recipient. Common examples include BEC, CEO fraud, payment diversion, and supplier impersonation.
Coverage can be difficult to classify because the transfer is often authorized by an employee, even though it occurred under deception. Depending on the insurer and policy wording, FTF may be handled in different ways:
- Cyber insurance: Social engineering/FTF coverage is often offered as an optional endorsement and may depend on specific triggers and definitions that differ by carrier.
- Commercial crime (fidelity) insurance: Many organizations look to crime coverage and/or specific social engineering endorsements for these scenarios, especially where cyber policy triggers do not clearly apply.
When included, social engineering and FTF coverage are commonly subject to lower sub-limits and more restrictive conditions than the policy’s broader incident response or liability protections.
Media liability and errors and omissions (E&O)
Media liability and errors and omissions (E&O) coverage address third-party claims that arise from published content, professional services, or failures to meet contractual obligations.
Media (or content) liability commonly addresses claims such as defamation and certain intellectual property allegations (for example, copyright or trademark-related claims) connected to published content, including digital communications. E&O coverage addresses claims alleging that professional services caused a customer financial loss due to an error, omission, or failure to perform as expected.
Unlike core first- and third-party cyber insurance, media liability and E&O are often optional endorsements within a cyber policy or provided under separate policies, and the scope varies by insurer, policy form, and the business’s activities.
Business interruption and extra expense coverage
Business interruption coverage may help address lost income and related expenses when a covered cyber event disrupts operations. In addition to attacks like ransomware, policies may also address disruption tied to certain technology failures, and some forms extend to outages at third-party providers (often described as contingent or dependent business interruption). Definitions and triggers vary by insurer and policy wording.
This coverage is often discussed in two parts:
- Direct business interruption: Disruption to the insured organization’s own systems.
- Dependent/contingent business interruption: Disruption caused by a covered outage at a third-party service provider (for example, a cloud or platform provider).
Policies frequently apply waiting periods and other constraints before business interruption coverage responds. Extra expense coverage may also apply for reasonable costs to keep operations running or speed recovery (for example, emergency technical support or alternative arrangements), depending on wording.
These costs can be substantial in disruption-heavy sectors. For example, the European Union Agency for Cybersecurity (ENISA) has cited a median cost of about €300,000 (approximately $356,000) for major cybersecurity incidents in the healthcare sector, largely driven by operational disruption and recovery activities.
System failure and bricking coverage
Some cyber policies include (or can add) coverage for losses tied to system failure: technology failing to work as intended, including non-malicious events in some forms, though availability and triggers vary across the market.
“Bricking” coverage (sometimes described as computer replacement coverage) generally addresses replacement costs when hardware is rendered permanently unusable due to a cyber event (commonly malware). This is typically offered as a specific coverage grant or endorsement rather than assumed in every policy.
Coverage for non-malicious system failure and for failures that resemble normal IT faults (for example, accidental malfunctions or bad updates) is especially policy-specific, so coverage depends on how the policy defines a covered event.
PCI and payment card coverage
This refers to costs that can arise after a payment card data incident, including assessments and response obligations tied to the Payment Card Industry Data Security Standard (PCI DSS) and card network rules. These costs can include investigation and remediation requirements, compliance-related expenses, and reimbursement claims from issuing banks for card reissuance and certain fraud losses.
PCI-related amounts are often treated as contractual assessments or penalties, which many cyber policies either exclude or only cover if they are expressly included. Where offered, PCI/payment card coverage is typically provided as a sub-limited extension or add-on and may come with strict conditions (for example, specific definitions of covered events and requirements tied to compliance or vendor use).
Which types of cyber insurance do different businesses need?
Cyber insurance needs vary by business size and industry due to differences in risk exposure, regulatory obligations, operational complexity, and reliance on third parties.
Note: Coverage structures and suitability depend on a business’s specific risk profile, policy wording, and applicable law. Organizations should consult licensed insurance professionals and legal counsel when evaluating coverage.
Cyber insurance for small businesses
Small businesses often use packaged cyber policies designed to cover common scenarios while keeping premiums and administration manageable. These policies typically combine first-party incident costs and third-party liability protection and frequently include access to incident-response support services (for example, forensic and legal assistance coordinated through the insurer).
Limited budgets, fewer internal response resources, and reliance on outside IT and cloud providers can make insurer-coordinated response support a higher practical priority than highly customized coverage structures.
Because limits are often lower and coverage grants narrower, some small-business policies may require add-ons for longer downtime scenarios, contingent business interruption tied to third-party outages, or certain fraud-and-transfer losses that arise from social engineering. Policy documents often address these areas through exclusions, sub-limits, waiting periods, or endorsements rather than default coverage.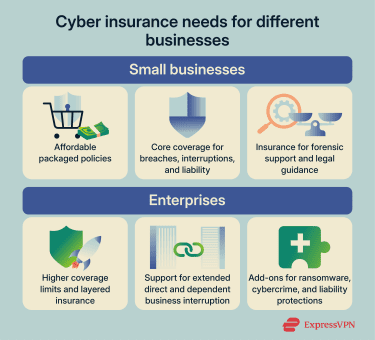
Cyber insurance for enterprises
Enterprises tend to face more complex cyber risk profiles due to larger data volumes, interconnected infrastructure, reliance on digital services, and multi-entity operations. They also often have broader third-party exposure, including potential claims from customers, suppliers, and partners.
These factors commonly drive higher limits and more layered insurance structures. Enterprise programs often prioritize:
- Comprehensive incident response support and higher breach-related limits.
- Longer business interruption periods and contingent business interruption options.
- Ransomware/extortion response and defined cybercrime-related endorsements.
- Privacy, network security, and legal defense protections.
Underwriting is typically more rigorous. Insurers often assess an enterprise’s security posture in detail and may condition pricing, terms, or eligibility on specific controls and governance practices.
Global operations can also complicate coverage decisions. Regulatory regimes differ across jurisdictions, and policy wording may treat defense costs, investigations, and fines/penalties differently depending on legal insurability and local requirements.
Industry-specific cyber insurance needs
Cyber insurance needs vary by industry because sectors differ in the types of data handled, tolerance for downtime, dependence on external providers, and regulatory exposure. These differences can influence which coverage extensions matter most and where sub-limits, triggers, and exclusions tend to be most consequential.
Healthcare organizations, for example, handle highly sensitive patient data and face strict breach-response obligations, which can increase the practical importance of incident response support, notification-related costs, and privacy liability.
Organizations providing critical or infrastructure-adjacent services (for example, financial services) often face heightened exposure to operational disruption and third-party dependency, which can make business interruption terms, contingent interruption options, and network security liability more relevant.
Merchants that process payment card data can be exposed to payment card ecosystem costs (including assessments and remediation obligations), which may require specific PCI/payment-card coverage grants or endorsements rather than relying on general regulatory expense language.
Third-party dependency can further complicate coverage decisions. Where operations depend on cloud platforms and other service providers, coverage can be narrower or structured with distinct triggers and sub-limits for dependent business interruption and related expenses.
Personal cyber insurance
Cyber risk is not limited to businesses. Individuals can also face costs and disruption from identity theft, account takeovers, and misuse of personal data exposed in breaches or sold by data brokers.
Personal cyber insurance typically refers to consumer-focused coverage and services that help detect misuse early and reduce the financial impact of identity-related fraud.
One example is ExpressVPN’s Identity Defender, which combines identity protection tools with a virtual private network (VPN) subscription. It includes ID Alerts (monitoring for signs of misuse or exposure), Data Removal (requests to remove personal data from data brokers and people-search sites), and Credit Scanner (credit monitoring alerts), plus up to $1 million in identity theft insurance for eligible losses.*
Identity Defender is currently available to U.S. users on select plans.
Read more: Identity theft insurance: What it is and whether it’s worth it
How cybersecurity measures affect insurance coverage
Cyber risk management measures can influence eligibility, coverage scope, pricing, and claims handling.
Underwriting commonly relies on questionnaires and supporting materials describing security controls and practices, and those statements can function as contractual representations in the insurance contract. In coverage disputes, insurers may argue that material misstatements or omissions in an application support rescission or denial, depending on the facts, policy language, and applicable law.
Many policies also include exclusions or conditions tied to “minimum required practices” or similar concepts, where failure to maintain specified controls can affect coverage for certain loss scenarios. The practical effect is that the strength and consistency of an organization’s controls can influence both the terms offered and how coverage is evaluated after an incident.
During underwriting, insurers evaluate how organizations prevent, detect, and respond to cyber incidents by reviewing controls such as:
- Endpoint security
- Identity and access management (IAM)
- Backup and recovery
- Incident response (IR) readiness
- Security governance
Organizations with weaker controls may face lower limits, narrower triggers, or tighter terms for high-severity losses (often including ransomware-related events and business interruption), depending on insurer appetite and the risk profile presented.
The role of remote access and identity controls
Remote access and identity controls frequently receive heightened underwriting attention because credential misuse and remote access weaknesses are common pathways into business systems. As part of underwriting, insurers commonly look for multi-factor authentication (MFA) on email, remote access, and privileged accounts, and may ask detailed questions about how remote access is implemented and controlled.
Some underwriting materials also explicitly reference modern access models such as zero trust network access (ZTNA) as one of the mechanisms used to secure remote access, alongside VPN and MFA-based approaches.
Strong authentication and access management can affect how insurers view loss frequency and severity risk, which can translate into differences in eligibility and coverage terms, particularly for ransomware- and intrusion-driven claims.
Read more: VPNs, firewalls, endpoint security: What does your team really need?
*The insurance is underwritten and administered by American Bankers Insurance Company of Florida, an Assurant company, under group or blanket policies issued to Array US Inc., or its respective affiliates for the benefit of its Members. Please refer to the actual policies for terms, conditions, and exclusions of coverage. Coverage may not be available in all jurisdictions. Review the Summary of Benefits.
FAQ: Common questions about types of cyber insurance
How many types of cyber insurance are there?
Cyber insurance generally consists of two main types: first-party and third-party coverage. Most policies combine both, covering direct losses to the insured business as well as liability to customers, partners, or other third parties. Depending on the insurer and risk profile, coverage may be offered as a bundled policy or supplemented with add-ons for specific risks.
Is cyber liability insurance the same as cyber insurance?
No, cyber liability insurance typically refers to third-party coverage for legal claims, regulatory response and defense costs, and, in limited cases, other amounts where legally insurable. Cyber insurance is broader and may include both cyber liability and first-party coverage, such as incident response, data recovery, and business interruption.
Do businesses need more than one type of cyber insurance?
Businesses often consider more than one type of cyber insurance to avoid coverage gaps. While many businesses rely on bundled cyber policies, certain risks may require separate policies or endorsements, such as cybercrime, media liability, or system failure coverage. The need for additional coverage depends on the business’s industry and risk profile.
Are ransomware and data breach insurance separate policies?
Usually, ransomware and data breach coverage are bundled within a first-party cyber insurance policy. Data breach coverage focuses on investigation and response costs, while ransomware or cyber extortion coverage may include ransom payments, negotiation services, and system restoration. Although part of first-party coverage, ransomware protection is often provided through endorsements and is subject to lower sub-limits.
Can cybersecurity tools impact required coverage types?
Yes, cybersecurity tools can influence coverage needs, risk exposure, and insurability. Different tools reduce different types of cyber risk, shaping which losses remain most exposed.
Organizations with strong preventive controls may place greater emphasis on liability and incident response coverage, while those with weaker controls against ransomware or fraud may require higher limits or specific coverage for extortion or cybercrime.
Take the first step to protect yourself online. Try ExpressVPN risk-free.
Get ExpressVPN