What is killware? How it works and how to stay protected

While most cyberattack methods are defined by their method or intent, killware is defined by its outcome. It’s an umbrella term for cyberattacks that lead to real-world physical harm, regardless of the tools or motives behind them.
This article explains what killware is, how it leads to harm, and which cybersecurity best practices can help reduce the risk of these attacks.
What is killware?
Killware is not a formal class of malware, like spyware or ransomware, but rather a term describing cyber incidents with consequences that extend into the physical world. It’s defined by the end result, not the attack method or the attacker’s motive.
Sometimes, the harm is intentional; in other cases, people can be hurt as a byproduct of critical systems being disrupted. What makes it killware is that the attack puts lives at risk, regardless of whether that was the original goal.
What makes killware different from traditional malware?
Malware is a broad term for any software designed to damage, disrupt, or steal from systems. This includes viruses, spyware, scareware, and ransomware. Killware is different because the stakes are higher, as it often affects systems where failure can lead to physical harm or death.
How killware attacks lead to real-world harm
Killware attacks cause harm when cyber incidents disrupt systems that people depend on for survival, safety, and essential services. When those systems fail, even temporarily, the effects can quickly move beyond digital inconvenience to serious physical consequences.
When attackers disrupt healthcare systems, emergency services may be diverted to other hospitals, treatments could be delayed, and access to critical care might be blocked.
When critical infrastructure is targeted, it can result in widespread panic, such as the attack on Colonial Pipeline in 2021. It shut down one of the largest U.S. fuel pipelines, causing panic buying that led to a regional gas shortage.
When large companies with interconnected systems are targeted, the damage can spread quickly. In one case, Norsk Hydro, an aluminum producer, was the target of ransomware. It affected 22,000 computers across 170 sites in 40 different countries. Some production lines were able to operate manually, but in many cases, they had to be shut down completely.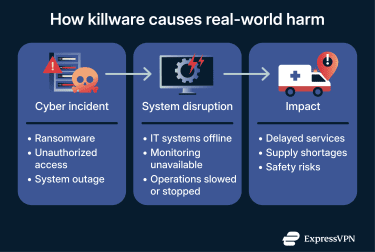
Examples of killware attacks
Killware risks can emerge in different ways. In some cases, cyberattacks target essential services like water or energy systems, where disruption or manipulation can cause direct physical harm.
In others, financially motivated ransomware disrupts critical services such as healthcare, creating serious safety risks as a byproduct of system outages.
The examples below show how both scenarios can lead to killware-level risk, even when the attacks themselves use common malware techniques.
Pro-Russia hacktivist attacks on U.S. SCADA systems (up to 2025)
In 2025, the Cybersecurity and Infrastructure Security Agency (CISA) issued an advisory stating that pro-Russia hacktivist groups had gained access to Supervisory Control and Data Acquisition (SCADA)-connected systems in U.S. critical infrastructure, including energy, water and wastewater, and agriculture.
The attacks relied on weak or default passwords, exposed remote access services, and brute-force login attempts. In some cases, attackers also launched distributed denial-of-service (DDoS) attacks to distract defenders while attempting to gain access.
These intrusions reached industrial control and human-machine interface systems. While no confirmed injury occurred and many incidents were detected quickly or limited in scope, that level of control carries real risk, including equipment damage, service outages, and safety hazards.
Oldsmar water treatment plant attack (2021)
In this attack, a hacker gained access to a computer system controlling the water supply in Oldsmar, Florida. The attacker increased the amount of sodium hydroxide (lye) in the water treatment system from 100 parts per million (ppm) to 11,100ppm.
A supervisor caught and reversed the change immediately, and remote access to the water system was disabled. No one was harmed and the plant continued its operations as usual.
Following the incident, the Cybersecurity and Infrastructure Security Agency (CISA) released a report saying that cybersecurity weaknesses, including poor password security and an outdated operating system, were the likely causes of the hack.
Ascension Health ransomware hit (2024)
In 2024, the Black Basta group attacked Ascension, one of the largest non-profit health systems in the U.S.
According to the HIPAA Journal’s report on the incident, the ransomware affected a large percentage of Ascension’s 136 hospitals across multiple states, shutting down access to electronic health records, patient portals, and internal communications. Staff were forced to divert ambulances, cancel medical procedures, and fall back on paper systems.
It took over a month to restore operations, during which a massive backlog of patient records piled up.
Who are the primary targets of killware?
Unlike typical cyberattacks, which end in data and financial theft, killware doesn't typically target individuals. Often, attackers target sectors that depend on interconnected systems designed for reliability and uptime, but not necessarily for cybersecurity.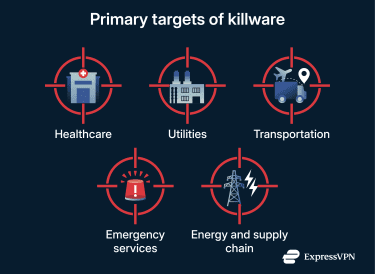
Healthcare
Hospitals, clinics, and pathology providers are frequent ransomware targets due to the critical nature of their systems. Patient care depends on digital systems, from electronic health records to diagnostic machines and drug delivery tools.
Ransomware attacks can cause canceled surgeries, diverted ambulances, and delays in treatment.
Utilities
Water plants and power grids increasingly rely on the industrial internet of things (IIoT), connecting physical controls to networks that were designed before modern threat models. If malware locks those systems or knocks them offline, critical operations stop running safely.
Transportation
Modern transport systems rely on digital control. From air traffic coordination to subway signals, everything runs on software. If an attack shuts those systems down, operators may have no choice but to cancel services.
That can delay ambulances, ground planes, or trap commuters. In a worst-case scenario, it can even cause accidents.
Emergency services
Every second counts in an emergency. If hackers use ransomware to lock up emergency call systems or shut down access to responder data, first responders are forced to work in the dark.
Dispatch calls may not go through, maps and routes can vanish, and crucial response time is lost. This delay could potentially be fatal.
Energy and supply chains
If ransomware hits energy networks or supply chains, the effects ripple quickly. Power generation, food delivery, and clean water all depend on systems running smoothly, and if attackers take down those systems, outages and shortages may follow.
Factors that increase risk
While killware incidents can look different across sectors, the underlying risk factors are often similar. Certain technical, organizational, and operational conditions make it easier for cyberattacks to escalate from digital disruption to real-world harm.
- Outdated systems and security gaps: Critical infrastructure facilities often run old software and unpatched systems that lack modern protections. These legacy technologies are easier for attackers to break into, giving ransomware groups a path to disrupt services.
- Connected systems: More digital connections mean more opportunities for attackers to find vulnerabilities and spread ransomware through critical infrastructure. For example, electronic records, networked devices, and third‑party tools create a complex web of entry points.
- Limited cybersecurity investment: Smaller and rural facilities in particular may lack dedicated cybersecurity teams, leaving them less prepared to prevent or respond to ransomware attacks.
- Pressure to restore systems quickly: The urgency to resume operations increases operational risk and may motivate attackers to target critical infrastructure.
- Phishing and weak remote access: Attackers frequently start ransomware campaigns with phishing emails or by exploiting remote access tools that lack strong authentication.
- Third‑party and supply chain weaknesses: Facilities often rely on vendors for software, equipment, and data services. If those partners have security gaps, attackers can navigate through these systems and move into multiple connected networks, increasing the likelihood of knock-on ransomware effects.
- Legacy operational technology (OT) in utilities and infrastructure: Water treatment plants and energy systems often rely on aging OT that wasn’t built with cybersecurity in mind. Many of these systems are now internet-connected but lack modern protections, creating the potential for attackers to trigger real-world harm.
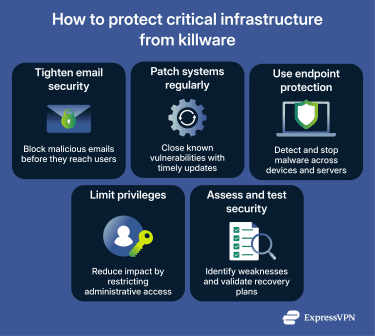
How to protect critical infrastructure from killware
Cybersecurity best practices
- Harden email security: Email is a potential delivery method for ransomware. Strong filtering, attachment scanning, and email authentication help prevent malicious messages and spoofed emails from reaching users.
- Patch systems regularly: Unpatched operating systems, software, and firmware are common entry points for ransomware. Regular updates reduce exposure to known vulnerabilities that attackers actively exploit.
- Use endpoint protection: These tools provide baseline protection by detecting and blocking known malicious activity across user devices and servers.
- Limit privileges: Excessive administrative access makes it easier for ransomware to spread once a system is compromised. Limiting privileges reduces how much damage an attacker can cause from a single account.
- Assess and test security: Vulnerability assessments, penetration testing, and backup testing help organizations understand their weaknesses and confirm that recovery plans will work if systems are disrupted.
Incident response and recovery plans
When ransomware breaches preventive defenses, response speed and coordination become critical. U.S. government guidance focuses on containing the incident, protecting recovery options, and reducing further harm.
- System isolation: Removing infected devices from the network helps prevent ransomware from spreading to shared drives and connected systems.
- Early shutdown: Isolating or powering off affected devices that are not fully encrypted may limit damage and preserve data.
- Backup protection: Taking backup systems offline and confirming they are malware-free helps preserve clean data for recovery.
- Law enforcement support: Reporting incidents to federal law enforcement can provide access to investigative assistance and resources and may be mandatory in some circumstances.
- Data preservation: Securing any unaffected or partially accessible data can support investigation and recovery efforts.
- Credential resets: Changing system and network passwords after isolating infected systems reduces the risk of continued access.
- Persistence removal: Removing malicious registry entries and files helps prevent ransomware from restarting.
Importance of cyber awareness training
Employee cybersecurity awareness training targets one of the most consistent causes of cyber incidents: human behavior.
According to the Verizon Data Breach Investigations Report, nearly 74% of data breaches involve the human element, often through phishing or social engineering.
Awareness training helps employees recognize suspicious emails, understand how attacks unfold, and act before small mistakes turn into serious incidents. When done well, training helps everyday staff strengthen security from within.
FAQ: Common questions about killware
What is killware, and how is it different from traditional malware?
Killware is a term used to describe cyberattacks that result in real-world physical harm or risk to human life. Traditional malware typically focuses on data theft, disruption, or financial gain. Killware is defined by its outcome, not its method.
Which industries are most vulnerable to killware?
Industries where downtime affects safety face the highest risk of killware attacks. This includes healthcare, utilities, transportation, emergency services, and energy supply chains. In these sectors, digital disruption can quickly translate into physical consequences.
What are the early warning signs of a killware attack?
Killware isn’t a specific type of software, so there are no unique technical indicators. However, the warning signs are the same as those of serious malware infections. These include system slowdowns, locked files, loss of access to critical systems, ransom messages, and unusual network activity.
How do organizations protect critical systems from killware?
Protection against killware starts with preventing common cyber incidents from escalating into physical harm. This includes staff training, strong email security, regular patching, access controls, reliable backups, and tested incident response plans.
Can individuals be targeted or affected by killware?
Killware, by definition, refers to cyberattacks that create a real risk of physical harm, not attacks aimed at specific individuals. While people are rarely targeted directly, they're often affected indirectly. Patients, commuters, and residents can face delayed care, service outages, or safety risks when systems that support healthcare, transportation, or utilities are disrupted.
Take the first step to protect yourself online. Try ExpressVPN risk-free.
Get ExpressVPN